Firewall Tutorial Point Pdf
Check Point technology is designed to address network exploitation administrative flexibility and critical accessibility. Configuring Supported Firewalls and Logs 3 Check Point VPN-1FireWall-1 v4x Versions Supported Check Point VPN-1 v 4x Check Point FireWall-1 v4x Obtaining Log Information You must specify the location of the Check Point firewall log file when you create a profile in Security Reporting Center.
Firewall Security Tutorialspoint
Learn Firewall Online At Your Own Pace.

Firewall tutorial point pdf. This Section introduces the basic concepts of network security and management based on Check Points three-tier structure and provides the foundation for technologies involved in the Check Point Architecture. The following configuration example shows a portion of the configuration file for the simple firewall scenario described in the preceding sections. Both hardware and the software can be used at this point to filter network traffic.
One works by using filters at the network layer and the other works by using proxy servers at. Check Point Solution for Network Address Translation 44 Public and Private IP addresses 44 NAT in FireWall-1 45 Static NAT 45 Hide NAT 46 Automatic and Manual NAT Rules 48 Address Translation Rule Base 48 Bidirectional NAT 49 Understanding Automatically Generated Rules 49 Port Translation 51 NAT and Anti-Spoofing 52 Routing Issues 52 IP Pool NAT 54. Check Point Tutorials Contents.
There are various tools and devices that can provide different security levels and help keep our private data secure. L2TP Layer 2 Tunneling Protocol L2TP is an IETF standard tunneling protocol that tunnels PPP traffic over LANs or public networks. Any local firewall setting created by a user even a local administrator is ignored.
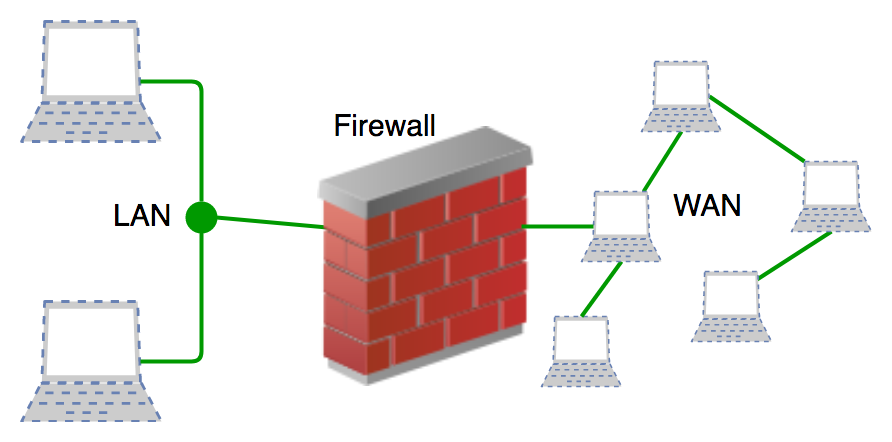
A local network. Firewalld provides a dynamically managed firewall with support for networkfirewall zones to assign a level of trust to a network and its associated connections interfaces or sources. Download free Computer Networking.
Installing VMware ESX 4. An area to protect. Internet Firewall Tutorial training course material a PDF file on 6 pages by Rob Pickering.
There is a separation of the runtime and permanent configuration options. Ip inspect name firewall tcp ip inspect name firewall udp. A business network staff to be protected.
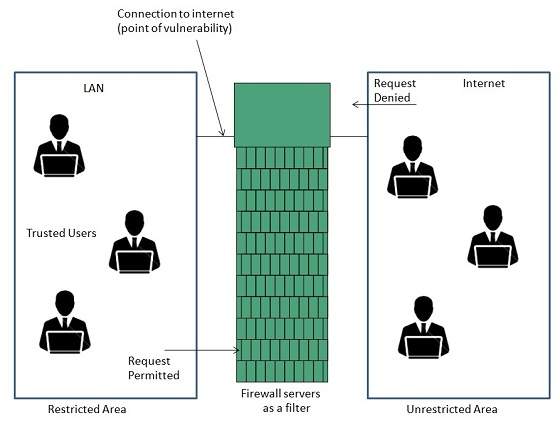
There are two types of Firewall system. Start Today and Become an Expert in Days. The connection between the two is the point of vulnerability.
Ensure that the firewall is enabled with your specified handling of network traffic and cannot be disabled. Ad Join Over 50 Million People Learning Online with Udemy. Learn Firewall Online At Your Own Pace.
Firewall inspection is setup for all tcp and udp traffic as well as specific application protocols as defined by the security policy. Cisco Systems developed the L2F protocol. It has support for IPv4 IPv6 Ethernet bridges and also for IPSet firewall settings.
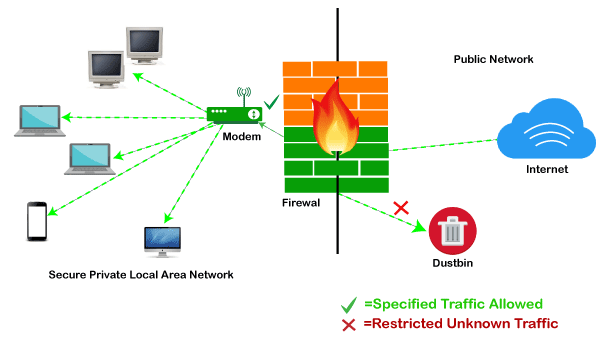
Download free Firewall Tutorial course material tutorial training PDF file by Cisco Systems on 21 pages. Check Point Firewall Security Solution In This Chapter Overview of Firewall Features 7 How to Use this Guide 9 SmartDashboard Toolbar 11 Overview of Firewall Features Firewalls control the traffic between the internal and external networks and are the core of a strong network security policy. Allow Remote Root Access Vmware ESX 4.
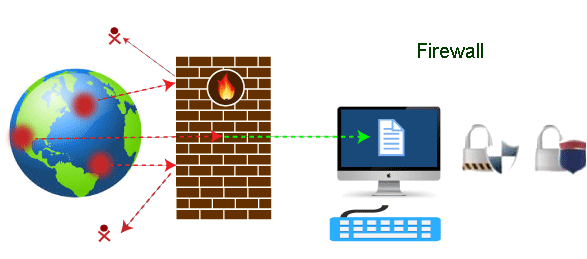
Start Today and Become an Expert in Days. The Firewall is a program or a hardware responsible for protecting you from outside world by controlling everything that happens especially all which must not pass between the Internet and the local network. Forwarding Point-to-Point PPP sessions from one endpoint to another across a shared network infrastructure.
Ad Join Over 50 Million People Learning Online with Udemy. Overlooked a network external to or intruders are suceptibles conduct to attacks. The computer does not display the notification when Windows Firewall with Advanced Security blocks a program from listening on a network port.
Nowadays it is a big challenge to protect our sensitive data from unwanted and unauthorized sources.
Firewall Firewall Tutorial Javatpoint
Firewall Firewall Tutorial Javatpoint
Introduction Of Firewall In Computer Network Geeksforgeeks

Types Of Firewall And Possible Attacks Geeksforgeeks