Access Matrix In Operating System Tutorial
Explain deadlock Avoidance in detailDEC 2015 3. Explain goals and principles of system protection in detail.

Need And Functions Of Operating Systems Geeksforgeeks
View protection as a matrix protection matrix Rows represent domains Columns represent objects Accessi j is the set of operations that a process executing in Domain i can invoke on Object j Dynamic protection Operations to add delete access rights.

Access matrix in operating system tutorial. Entries within the matrix indicate what access that domain has to that resource. Access matrix is used to define the rights of each process executing in the domain with respect to each object. Most of the operating systems access the file sequentially.
In sequential access the OS read the file word by word. Information in the file is processed in order one record after the other. From these approaches of decomposition three implementation of access matrix can be formed which are widely used.
In other words we can say that most of the files need to be accessed sequentially by the operating system. For example editor and compiler usually access the file in this fashion. The content is described in detailed manner and has the ability to answer most of your queries.
Memory management unit of OS needs to convert the page number to the frame number. A protectiondomain specifies the set of resources objects that a process can access and the operations that the process may use to access such resources. The access matrix is used to define the protection domain of a process.
Explain deadlock recovery in detail. We have designed this tutorial after the completion of a deep research about every concept. The rows of matrix represent domains and columns represent objects.
The inefficiency can be removed by decomposing the access matrix into rows or columnsRows can be collapsed by deleting null values and so for the columns to increase efficiency. It is the simplest access method. They are as follows.
What is Access matrix. This mode of access is by far the most common. What is Access Matrix.
Lets look at various ways to access files stored in secondary memory. Our Operating system tutorial is designed for beginners professionals and GATE aspirants. Read and write make up the bulk of the operation on a file.
The logical address has two parts. The model of protection that we have been discussing can be viewed as an access matrix in which columns represent different system resources and rows represent different protection domains. By examining the rows in the access matrix one can see all the operations that a subject is.
When a page is to be accessed by the CPU by using the logical address the operating system needs to obtain the physical address to access that page physically. Each cell of matrix represents set of access rights which are given to the processes of domain means each entryi j defines the set of operations that a process executing in domain Di can invoke on object Oj. Loads operating system kernel and starts execution Computer System Organization Computer-system operation One or more CPUs device controllers connect through common bus providing access to shared memory Concurrent execution of CPUs and devices competing for memory cycles Computer-System Operation IO devices and the CPU can execute concurrently.
Explain deadlock prevention in detail.
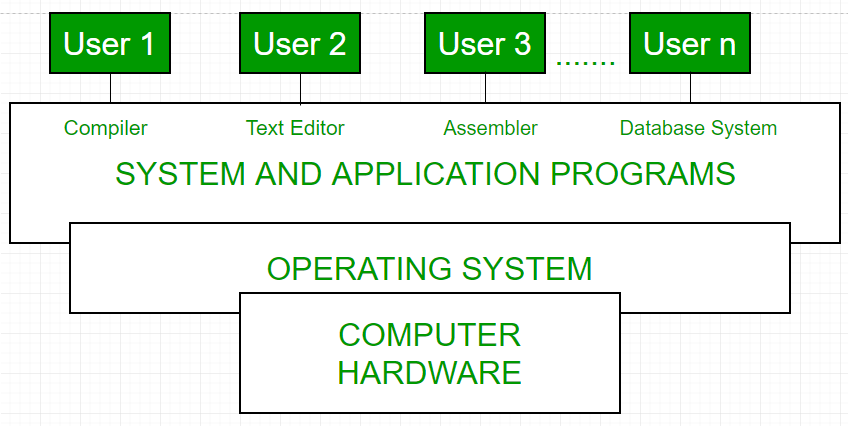
Introduction Of Operating System Set 1 Geeksforgeeks
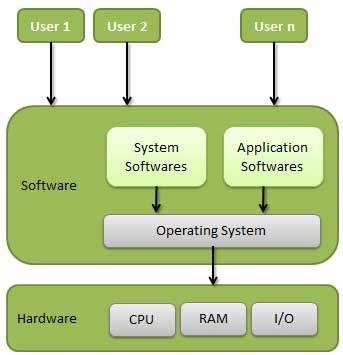
Operating System Quick Guide Tutorialspoint

Operating Systems Operating System Programming Tutorial Computer
